Figure 1 from Data communications in electricity supply chain: ICT-systems interconnections in Nordic power market area | Semantic Scholar
Computation | Free Full-Text | Stochastic Modeling with Applications in Supply Chain Management and ICT Systems

Figure 1.1 from The role of information and communications technology (ICT) in supply chain management (SCM) in distributor perspective - a study of distributor company of automotive parts in Klang area | Semantic Scholar

CISA releases ICT supply chain risk management task force year 2 report | 2020-12-18 | Security Magazine

ICT Supply Chain Integrity: Principles for Governmental and Corporate Policies - Carnegie Endowment for International Peace
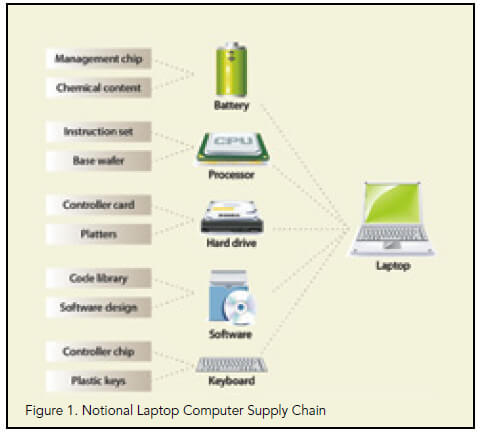
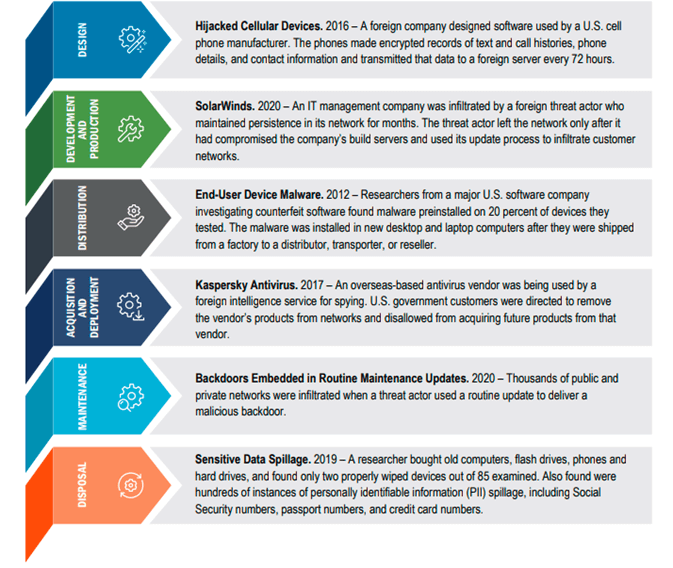
ICT Supply Chain Risk (Source: NIST Special Publication 800-161 Supply... | Download Scientific Diagram

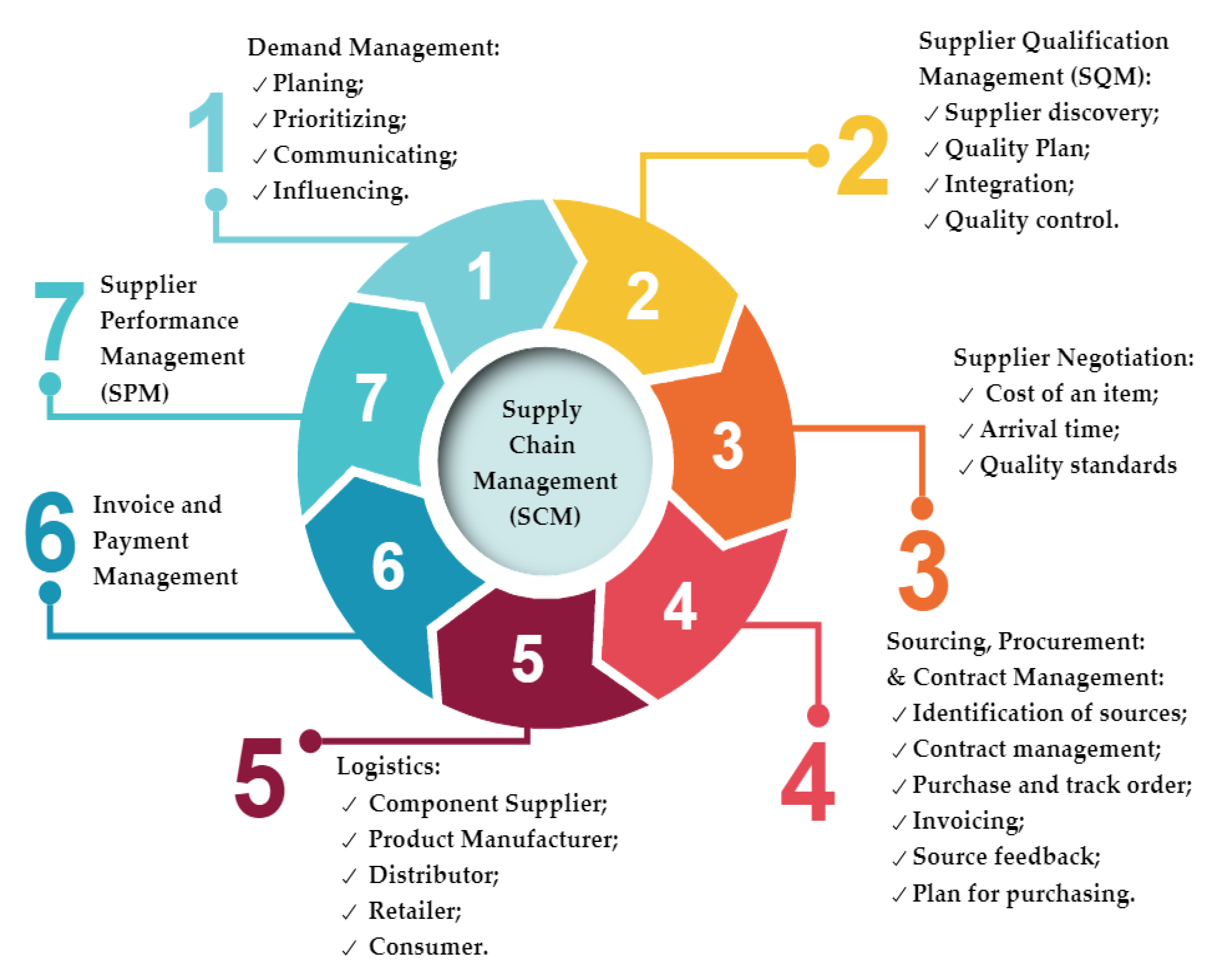
ICT in Supply Chain Management. Information represents a fundamental… | by Stefano Zambrini | Medium